To give your users easy access to your cloud apps, Microsoft Entra ID supports a broad variety of authentication protocols including legacy authentication. However, legacy authentication doesn’t support things like multifactor authentication (MFA). MFA is a common requirement to improve security posture in organizations.
Based on Microsoft’s analysis more than 97 percent of credential stuffing attacks use legacy authentication and more than 99 percent of password spray attacks use legacy authentication protocols. These attacks would stop with basic authentication disabled or blocked.
Today, most compromising sign-in attempts come from legacy authentication. Older office clients such as Office 2010 don’t support modern authentication and use legacy protocols such as IMAP, SMTP, and POP3. Legacy authentication does not support multifactor authentication (MFA). Even if an MFA policy is configured in your environment, bad actors can bypass these enforcements through legacy protocols.
User impact
Users accessing apps that don’t support modern authentication will no longer be able to access them with this policy enabled.
This policy shall be applied to all of your Microsoft 365 users in the organization.
Prerequisites
You should have at least Azure Active Directory Premium P1 subscription.
Steps:
- Login to Microsoft Entra
- From the Left Pane go to Protection and click on Conditional Access
- From the Right Pane, click on Create new policy
- Assign the name of the policy that you want, Eg: Policy to block legacy authentication (I used this name in my environment).
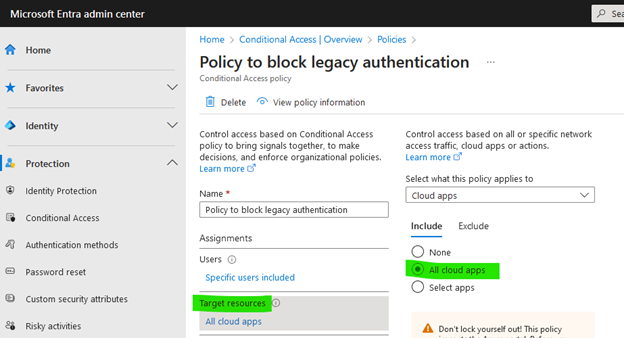
- Under Users select All Users
Note: if you prefer to test first which usually makes sense, then select, Select users and groups and select the test users.
- Under Target resources, select All cloud apps.
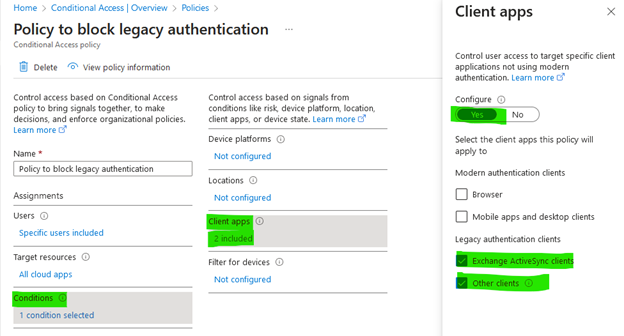
- Go to Conditions, go to Client Apps, set the toggle bar to Yes and under Legacy authentication clients select Exchange ActiveSync clients and other clients.
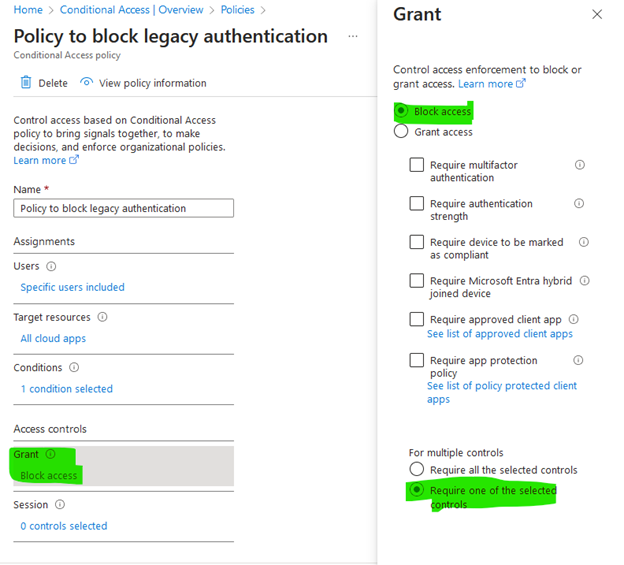
- Under Access controls select Grant, Under Control access enforcement to block or grant access, select Block access under For multiple controls select Require of the selected controls. Then click on
- Under Enable Policy, set the toggle to On.
Identify legacy authentication use
Before you can block legacy authentication in your directory, you need to first understand if your users have client apps that use legacy authentication.
Sign-in log indicators
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Identity > Monitoring & health > Sign-in logs.
- Add the Client App column if it isn’t shown by clicking on Columns > Client App.
- Select Add filters > Client App > choose all of the legacy authentication protocols and select Apply.
- If you’ve activated the new sign-in activity reports preview, repeat the above steps also on the User sign-ins (non-interactive) tab.
Filtering shows you sign-in attempts made by legacy authentication protocols. Clicking on each individual sign-in attempt shows you more details. The Client App field under the Basic Info tab indicates which legacy authentication protocol was used.
These logs indicate where users are using clients that are still depending on legacy authentication. For users that don’t appear in these logs and are confirmed to not be using legacy authentication, implement a Conditional Access policy for these users only.