Microsoft365 Security Baseline using PowerShell (CISA – SCuBA Project)
Microsoft365 Security Baseline using PowerShell (CISA – SCuBA Project)
Ensuring data and system security is fundamental for any services running in the cloud. Cloud and Infrastructure Architects do always want to monitor and generate reports based on which they can take necessary steps and tighten the security and keep protecting the environment from any ransomware attacks.
Maintaining Microsoft 365 security baseline with multiple admin centers quite takes a lot of time for the administrators.
CISA (Cybersecurity and Infrastructure Security Agency) has launched a project last year Dec’23 named Secure Cloud Business Applications (SCuBA), which provides guidance and capabilities to secure agencies’ cloud business application environments and protect federal information that is created, accessed, shared and stored in those environments.
SCuBA will help secure Federal Civilian Executive Branch (FCEB) information assets stored within cloud environments through consistent, effective, modern, and manageable security configurations for Microsoft 365 & Google Workspace Secure Configuration Baselines.
This document is more inclined towards Microsoft 365 security base line for the below listed services:
1. Microsoft Defender for Office 365
2. Microsoft Azure Active Directory
3. Microsoft Exchange Online
4. Microsoft SharePoint and OneDrive for Business
5. Microsoft Power BI
6. Microsoft Power Platform
7. Microsoft Teams
Let’s go through the steps and see how to generate the Microsoft 365 baseline report.
Steps
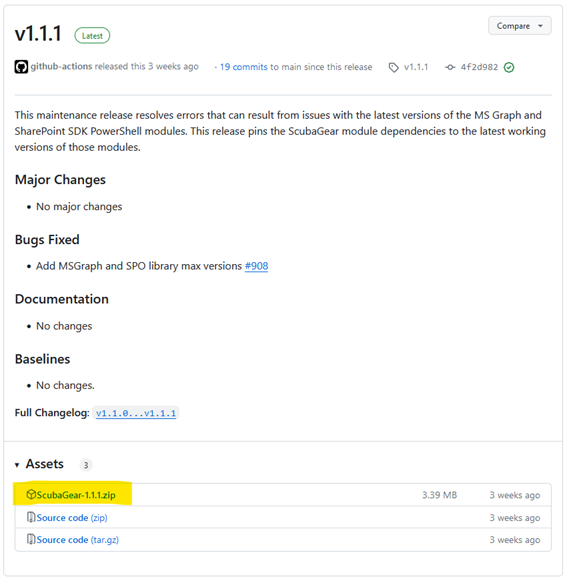
Step 1: Download the zip file from the latest release of Scubagear from GitHub from the official site.
Step 2: Extract the ZIP File; I would prefer to keep the extracted folder in C:\Temp.
Step 3: Run ScubaGear SetUp.ps1 located in C:\Temp\ScubaGear folder and import the ScubaGear module.
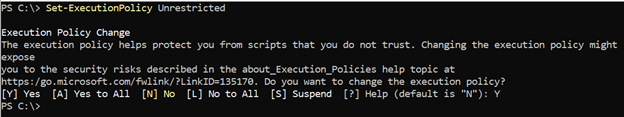
On Windows clients, the default execution policy is Restricted.
In this case, Set-ExecutionPolicy RemoteSigned or Unrestrictred should be invoked to permit ScubaGear to run.
Set-ExecutionPolicy Unrestrictred
Step: 4 Importing the module
Note:
Only PowerShell 5.1 is currently supported. PowerShell 7 may work, but has not been tested. Full PowerShell 7 support will be added in a future release.
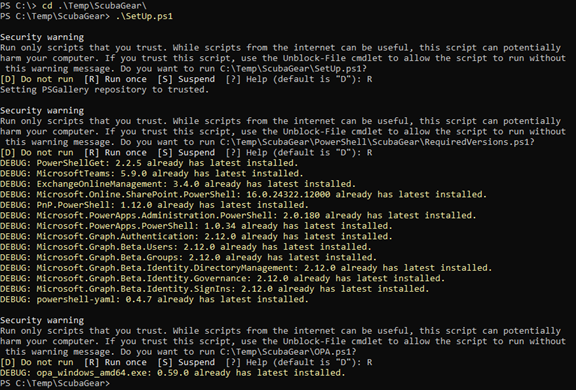
Run the SetUp.ps1 from C:\temp\ScubaGear to import all the dependencies and run all the scripts when prompted by pressing “R”.
If you can see in the above image, for me all the modules are installed since I already executed this earlier.
There is a chance that you might get an error “unable to download OPA”. You can download OPA from here and move to C:\temp\ScubaGear.
Below is the OPA version output.
Step 5: Run ScubaGear PowerShell script.
PS C:\Temp\ScubaGear> Import-Module -Name “C:\Temp\ScubaGear\.\PowerShell\ScubaGear”
Step 6: Run the script against all the products to generate a report.
Invoke-SCuBA
Run an assessment against Microsoft Entra ID with custom report output location
Invoke-SCuBA -ProductNames aad -OutPath C:\ Temp\ScubaGear
when you run the scripts against all or multiple products, it will ask you to login so that the tool can access your M365 environment and generate the report. Use the Global Admin credentials.
Step 7: You can view the output by running the BaselineReports.html
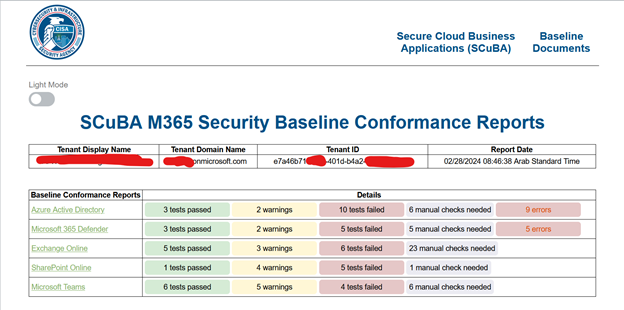
The report shall look like this:
Click on the Product under Baseline Conformance Reports to know more details.
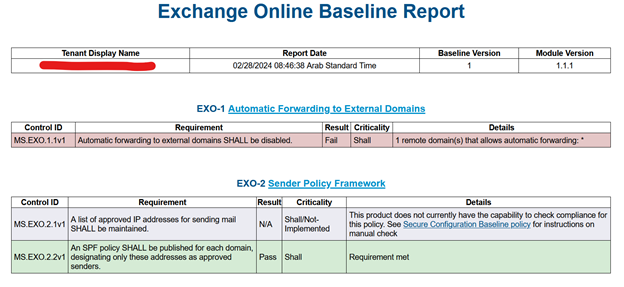
I clicked in Exchange Online.
The Exchange Online report shows that everything is fine
To learn more about CISA’s – Secure Cloud Business Applications (SCuBA) Project, click on the below link
Secure Cloud Business Applications (SCuBA) Project