Stopping Exchange 2016 Internal SPAM Spoofing
Stopping Exchange 2016 Internal SPAM Spoofing
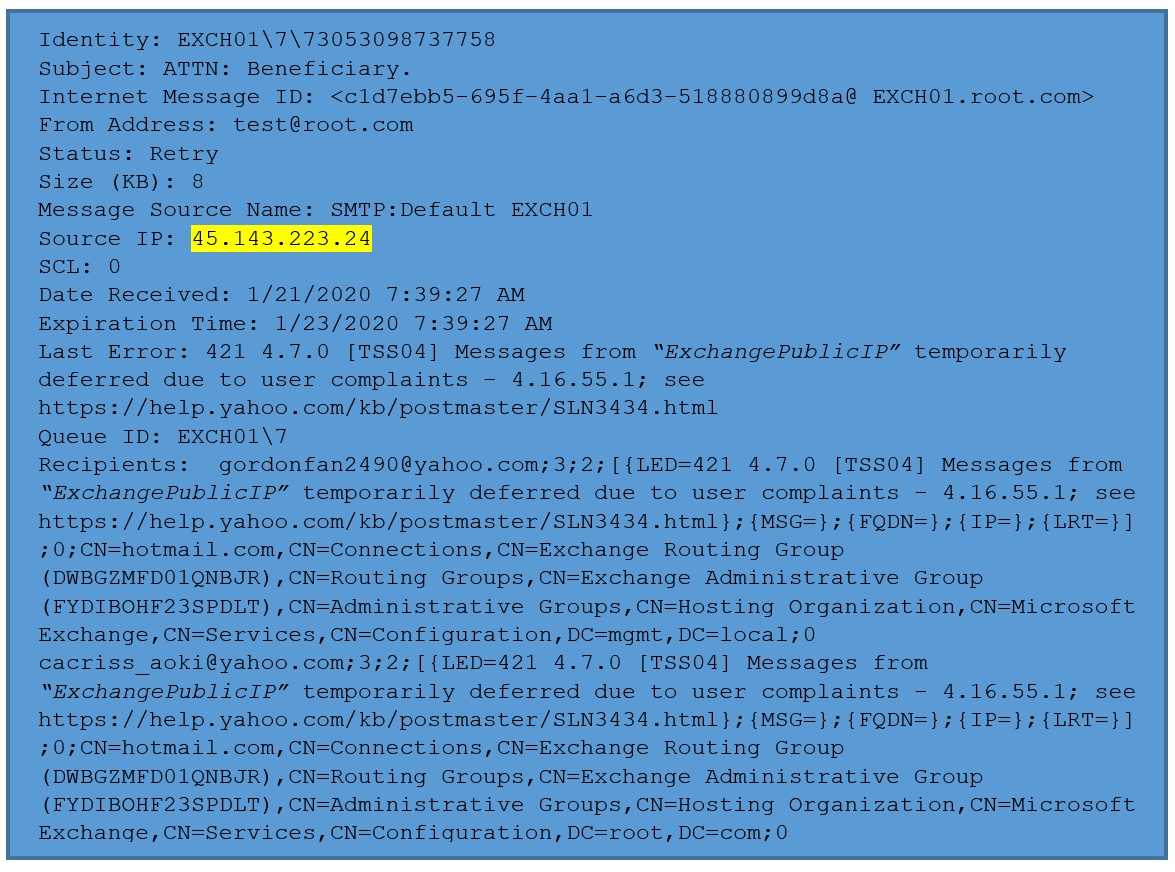
Exchange Server 2016 Multi-Tenant Environment. Root Domain for example root.com
I have a huge list of tenants in Exchange Servers, Let’s say: tenant1.com, tenant2.com, tenant3.com and so on….
Public and Internal DNS records for all the domains are created and working fine. Suddenly Exchange Servers started sending out SPAM emails using postmaster@root.com to abc@anydomain.com which doesn’t existing in Exchange and Exchange Queues use to pileup in 100’s and 1000’s. Which was becoming the major cause of IP getting blacklisted.
However, the best places we found to combat this involved removing the permission: ms-exch-smtp-accept-authoritative-domain-sender in the active directory for the receive connectors.
On all the Exchange Server 2016 run the following:
Get-ReceiveConnector “Default <name>” | Get-ADPermission -user “NT AUTHORITY\Anonymous Logon” | where {$_.ExtendedRights -like “ms-exch-smtp-accept-authoritative-domain-sender”} | Remove-ADPermission
And restart the Microsoft Exchange Frontend Transport Service on all the Exchange Servers.
It solved the problem.
Thanks to Eric Stevens for the guidelines mentioned in his blog. (https://infinitewebdesign.com/2016/08/12/stopping-exchange-2016-same-domain-spam-spoofing/)
Additionally, I would also recommend to have a close look on the IPs added into the Relay Connector which can also be one of the reason of SPAM Spoofing and uncheck “Anonymous Users” under Security.