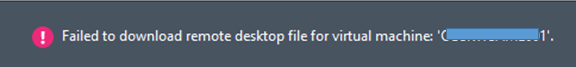
I have been trying to resolve the console connect issue since a long time, I involved my colleague to help me in resolving the issue.
We completed the following steps successfully but still the error exists:
- Issuing the certificate
- Installing the certificate on all the Hyper-V Hosts
- Installing the Certificate on SCVMM Server and Hyper-V Host by using the below script by running
## Variables
# Path to PFX file
$MyPFX = Get-ChildItem “\\servername\c$\Temp\rdgw.pfx”
# Password of the PFX
$PWD = Read-Host –AsSecureString
# VMM FQDN server name.
$VMM = “vmm.contoso.com”
## Main Code
Set-SCVMMServer -VMMServer $VMM `
-VMConnectHostIdentificationMode FQDN `
-VMConnectGatewayCertificatePath $MyPFX `
-VMConnectGatewayCertificatePassword $PWD `
-VMConnectHyperVCertificatePath $MyPFX `
-VMConnectHyperVCertificatePassword $PWD `
-VMConnectTimeToLiveInMinutes 1
Get-SCVMHost -VMMServer $VMM | Read-SCVMHost
- Installing the certificate on the Remote Desktop Gateway Server
- Registering the thumbprint of the certificate on the Remote Desktop Gateway Server by running
## Variables
# Server FQDN
$Server = “FQDN of the RDSGW SERVER”
# Certificate Thumbprint
$certTP = “cf9e0f307d81ff447195c5c11614f89e7fd45112”
## Main code
$RDSSet = Get-WMIObject -ComputerName $Server -NameSpace “root\TSGatewayFedAuth2” -Class “FedAuthSettings”
$RDSSet.TrustedIssuerCertificates = $CertTP
$RDSSet.Put()
After further trouble shooting we looked at the template that we used to create the certificate and the error was in the template itself.
Followed the below steps in order to create the certificate template for Console Connect and steps mentioned above then the issue was resolved.
Define Certificate Template for Trust Relationship
The certificate used to create a trust relationship between the VMM Management Server, Remote Desktop Gateway and Hyper-V hosts has a few special property requirements. Specifically, this certificate must include an Enhanced Key Usage (EKU) field that contains the Client Authentication object ID, it must support the SHA256 hash algorithm, and it must have a 2,048 bit or longer key length. Since these requirements are unique in comparison to many of the default certificate templates included with the installation of Active Directory Certificate Services, we’ll create a new certificate template on our CA server for issuing the appropriate certificate for remote console connections.
Complete the following steps on the server installed with Active Directory Certificate Services and configured as your Enterprise CA:
- Launch the Server Manager tool, and select Tools| Certificate Authority from the top menu bar.
- In the Certification Authority window, expand your CA server name in the left navigation pane.
- In the Certification Authority window, right-click on Certificate Templates in the left navigation pane, and then click Manage on the right-click pop-up menu.
- In the Certificate Templates Console window, right-click the Smartcard Logon template in the center pane, and then click Duplicate Template on the right-click pop-up menu.
- In the Properties of New Template window, click the General tab and then enter Remote Console Connect in the Template Display Name field.
- In the Properties of New Template window, click the Cryptography tab and then enter the following field values:
Minimum key size: 2048
Requests must use one of the following providers: Selected
Providers: Microsoft Enhanced RSA and AES Cryptographic Provider
- In the Properties of New Template window, click the Subject Name tab and then select the radio button option for Supply in the request.
If prompted with a warning dialog box, click the OK button in the dialog box to acknowledge the warning message.
- In the Properties of New Template window, click the Security tab and then ensure that your Active Directory username is listed with Enroll permissions.
- In the Properties of New Template window, click the OK button.
- Close the Certificate Templates Console window.
- In the Certification Authority window, right-click on Certificate Templates in the left navigation pane and then select New | Certificate Template to Issue.
- In the Enable Certificate Templates window, select the Remote Console Connect certificate template and then click the OK button.
An appropriate certificate template for issuing the certificate for validating a trusted relationship between the VMM Management Server, Remote Desktop Gateway and Hyper-V hosts is now defined and enabled for new certificate requests.
Refer to the below Microsoft TechNet Link where all the details are mentioned step by step